
Ransomware attackers are going after schools
One Friday in July, just before the start of the school year, Caroline Sice was out to lunch with a friend when she got an alarming call from a colleague. Lanesend Primary — a school on the Isle of Wight in the U.K., where Sice has been head teacher for 12 years — had been hit by a ransomware attack. All of the information stored on its network was completely inaccessible.
“Everything had been encrypted,” said Sice. “All the children’s records, staff records, all the teaching and learning, all the data, all the finances, internet. Everything.”
Lanesend Primary, which serves roughly 400 students, aged four to 11 years old, had experienced IT problems the day before. Staff couldn’t access their emails or remotely log into the school’s systems. Sice was aware of the issues, but attributed them to routine maintenance.
“I really, really hadn’t thought that it would be a cyber attack,” she said.
Ransomware: The New Disinformation
Malware whacks a computer like a mugging. Meanwhile, ransomware — the new gang on the corner — looks a lot like a kidnapping, taking digital files or whole computer networks hostage. Only a sizable, sometimes enormous payout, usually in cryptocurrencies, buys freedom. They are schemes to defraud and steal, and the intent is criminal.
Or is it much more than that?
Ransomware’s parallels with disinformation are striking. While most high-profile ransomware attacks are in the U.S., U.K., and Europe, the vast majority of attacks are in countries facing political instability, like in Latin America and Africa.
Many digital hostage-taking organizations originate from the same hotbeds where disinformation campaigns are generated, like Russia, Ukraine, North Korea, and the Philippines. Ransomware travels the same political divisions as disinformation campaigns, trafficking in the exploitation of economic inequality, fear of immigrants, and racial resentments to undermine public trust in institutions and belief in social stability.
Where disinformation uses noise and incoherence to sow doubt and spread division, ransomware does something similar: it, too, is an agent of chaos. It may look like just a way to make a crypto-buck, but its effects, very often intentional, are much more profound.
Lanesend was not the main target. The Isle of Wight Education Federation (IWEF), a multi-academy trust of three secondary schools, serving a total of over 2,000 students, provides technical support and data storage for Lanesend and two other primary schools on the island. A week into the summer holiday, its systems and those of the six schools for which it is responsible were crippled by hackers.
To regain access to them, a ransom of more than $1 million was demanded from IWEF. Payment was to be made in bitcoin, as has become common in similar attacks, but IWEF refused to comply. Now, it faces massive administrative disruption and thousands of dollars’ worth of bills to recover.
A worsening trend
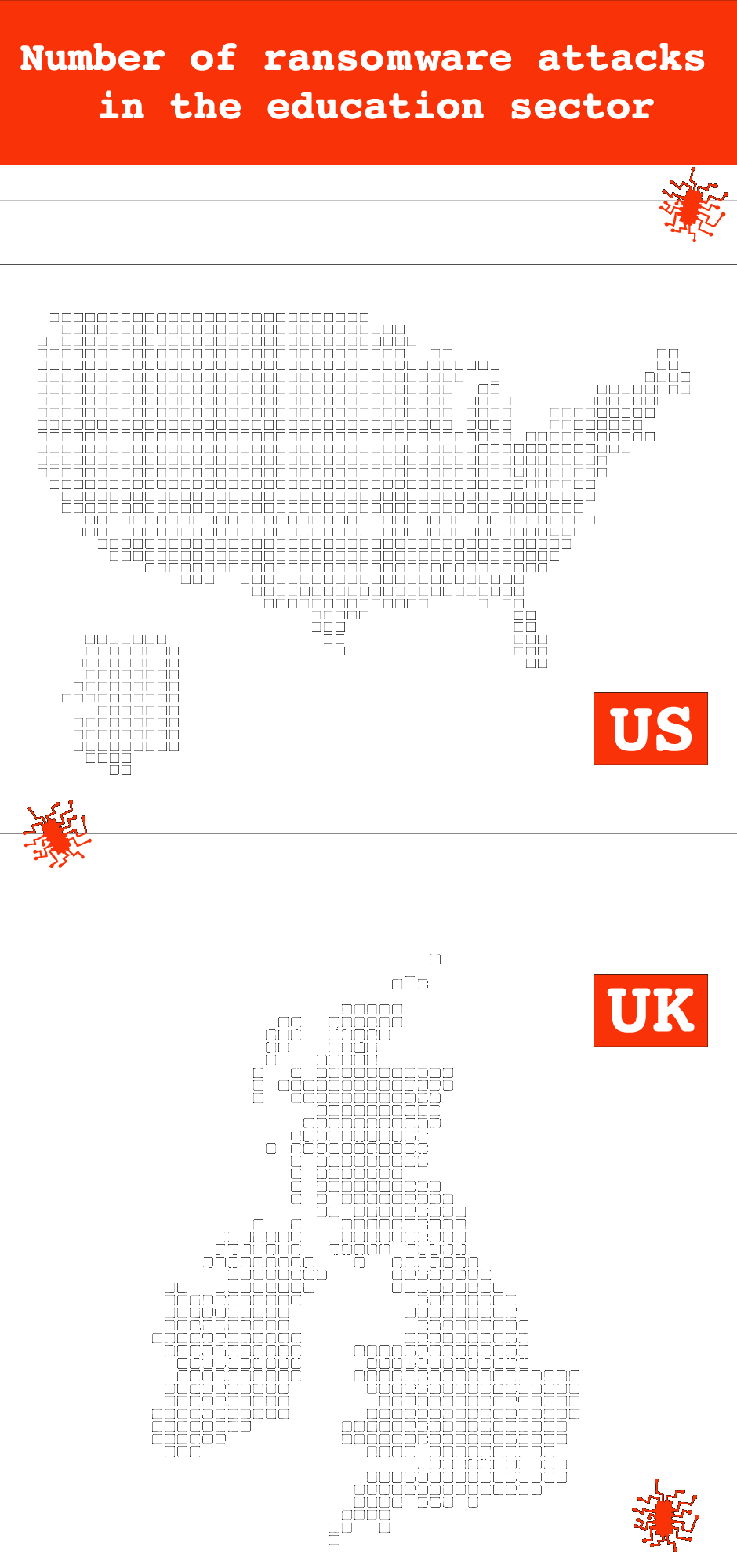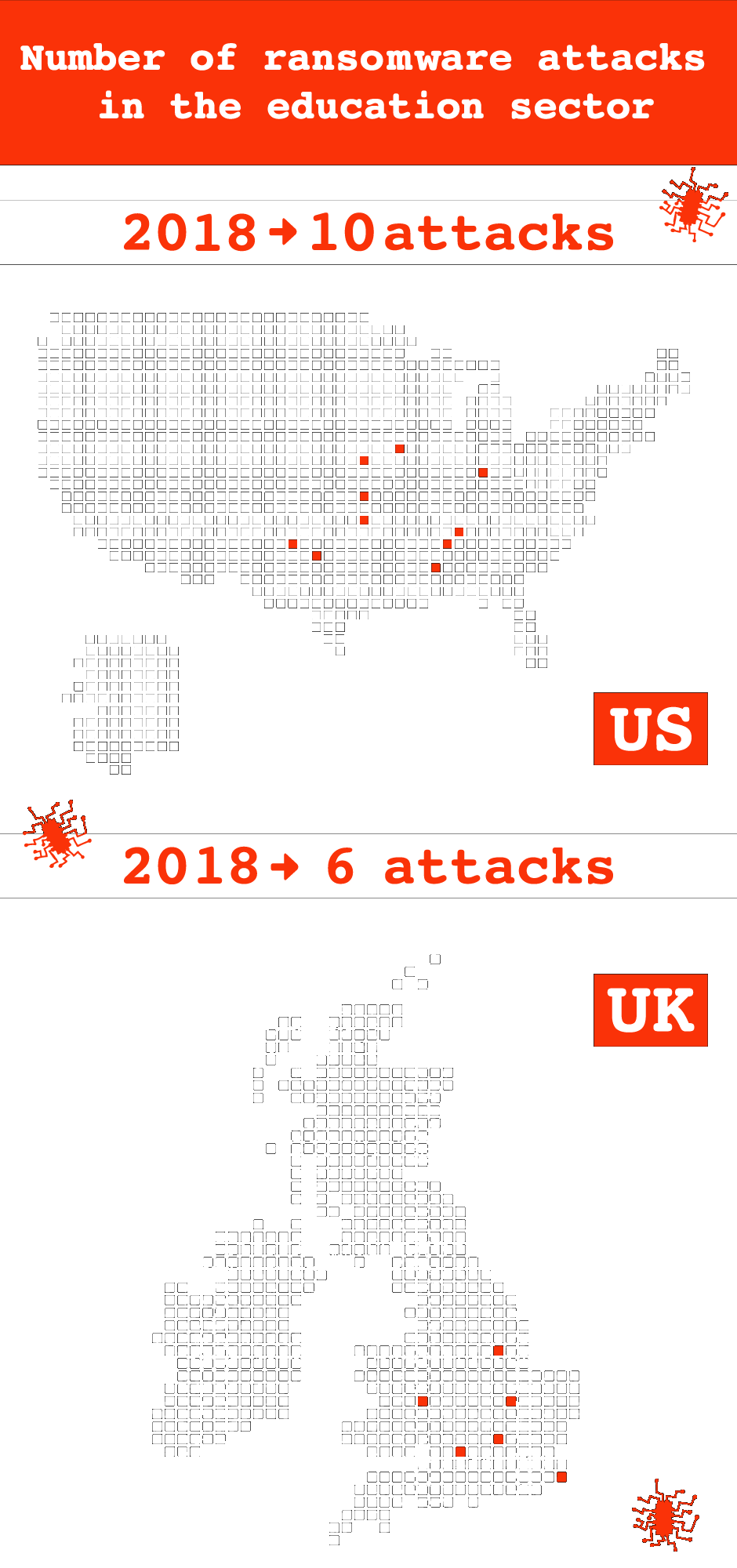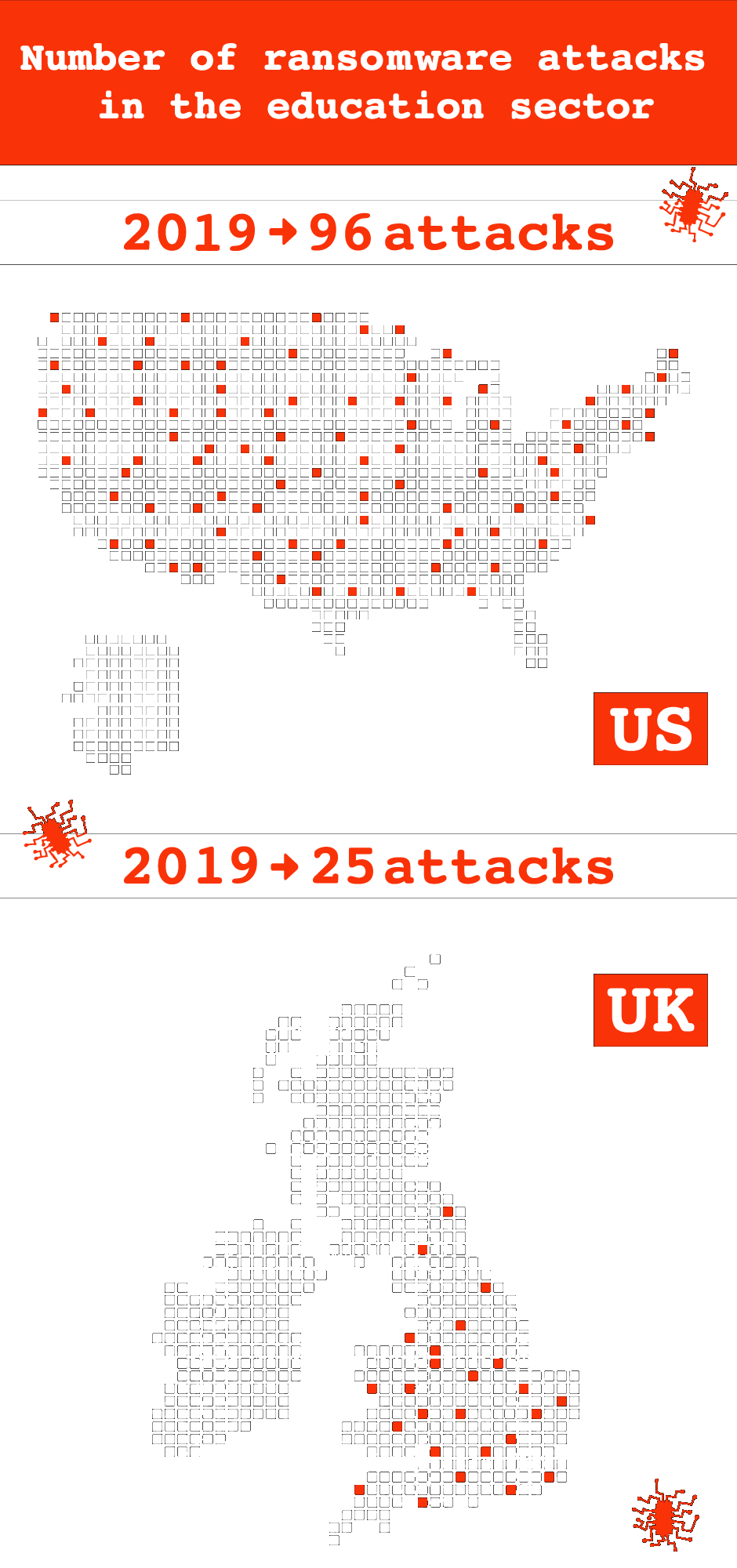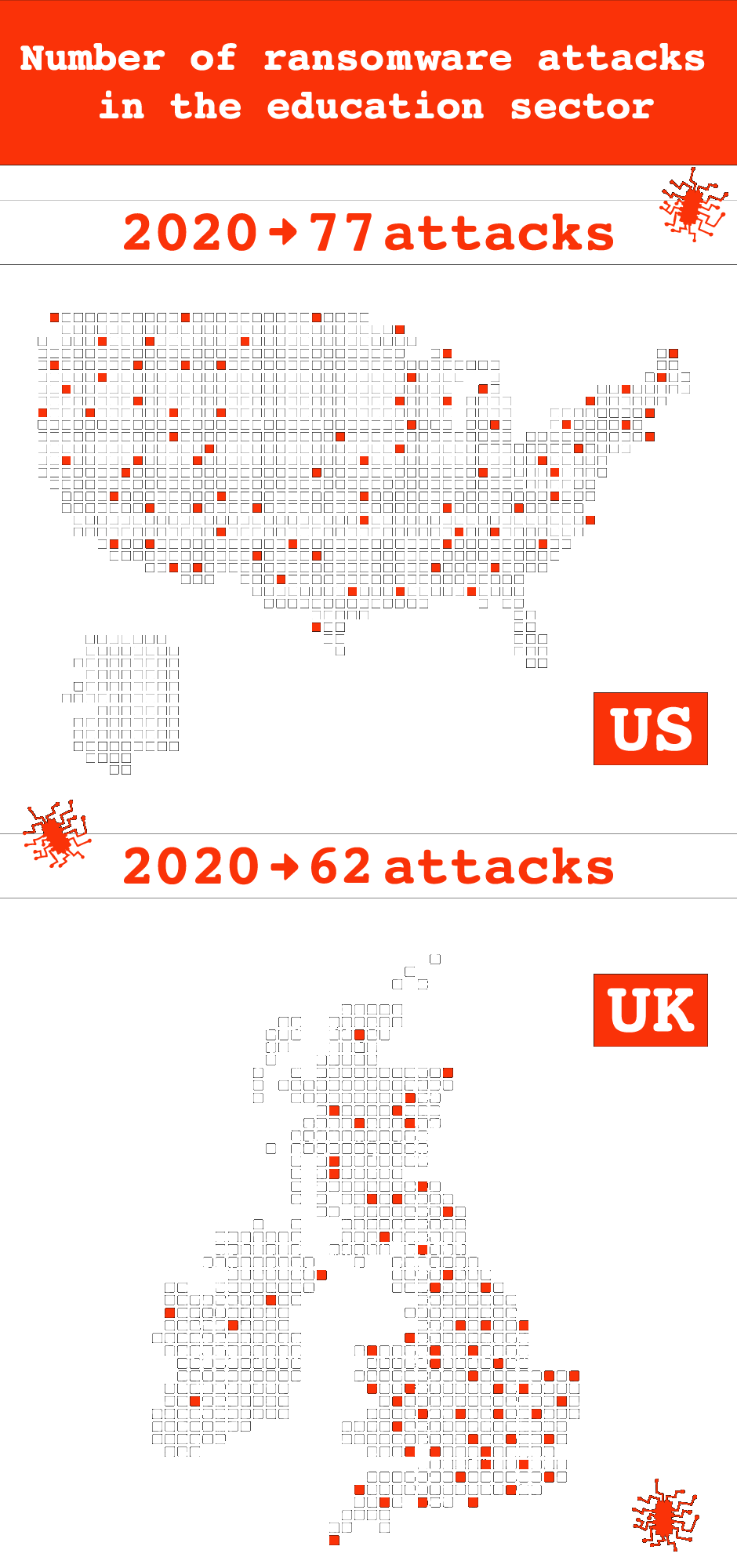
In recent years, education has become one of the sectors most frequently subjected to ransomware attacks. According to one British independent authority, the Information Commissioner’s Office, the number launched against U.K. universities and schools increased by 148% between 2019 and 2020.
In the U.S., however, the figures are even more stark. Attacks on schools from kindergarten through to 12th grade increased by 860% in 2019 — a record high. In July that year, the governor of Louisiana declared a state of emergency after three school districts were taken offline, just weeks before students were set to return from summer vacation. The number of incidents involving educational institutions decreased slightly in 2020, but the targets have become much bigger, including large school districts with higher budgets. In total 1.36 million American students were potentially affected last year alone.
The problem has become so bad that the Federal Bureau of Investigations and the U.K.’s National Cyber Security Center have warned schools about a growing number of attacks that have exploited increased cybersecurity weaknesses connected to remote learning during the pandemic.
According to Doug Levin, founder of the K-12 Cybersecurity Resource Center, which helps schools improve cybersecurity and conducts an annual study of ransomware attacks in the U.S., hackers are also demanding more money.
Levin first started tracking the phenomenon in 2015. “The extortion demands for schools at the time were $5,000, $10,000, $25,000,” he said. “It’s not unheard of for those ransomware demands to be $1 million or more now. That’s a dramatic change.”
After a hack in March, the Harris Federation, which runs 50 primary and secondary schools in London, received a ransom request for $4 million. But that was nothing compared to the demand issued to Broward County Public Schools of Florida in March, which came in at a whopping $40 million. The district refused to pay.
The ransom faced by IWEF was nowhere near that high, but it was still far beyond the organization’s means. “They asked for an amount that we couldn’t afford,” said executive headteacher Matthew Parr-Burman. “It was an easy decision, because it was like. ‘Well, this is a stupid amount.”

So, why schools?
Educational institutions can be a lucrative option for hackers — especially in parts of the U.S., where high property taxes contribute to big budgets, explained Levin.
As for the $40 million demand received by Broward County Public Schools, the district’s annual revenue sits at $4 billion. While that figure is not actually enough to meet the needs of the sixth largest school district in the United States, it’s still enough to be very attractive to cyber-criminals.
Schools are also a relatively soft target. Unlike major corporations, educational institutions rarely employ cybersecurity experts and their IT teams are often spread thin, tasked with both keeping their networks safe and more routine technical needs.
Many schools use older versions of software, with unpatched vulnerabilities, and frequently fail to put in place basic security measures. The Isle of Wight Education Federation, for example, had not enabled two-step authentication.
“Everything has been run for the convenience of the teacher, which is obviously quite convenient for a hacker too,” Parr-Burman explained.
That changed after the ransomware attack. Now, IWEF is one of many around the world directing significant resources towards the strengthening of its cybersecurity.
“The fact of the matter is that, in the last five or so years, school districts have flipped from where technology is a nice thing to have to it being really integral to their operations, not just in the classroom but in the back office,” said Levin.
He went on to explain that everything from locks on doors to telephone systems and school bus routing is now controlled and organized by computers. The growing reliance on technology seen during the pandemic could leave schools even more exposed.

According to Levin, distance learning could “increase the threat profile of school districts, because now you have people working on their personal networks and personal devices.” It is also likely that disruptions will be felt more widely in education systems with remote learning at their core. In September, a ransomware attack forced Howard University in Washington, D.C. to cancel all of its online classes.
Like hospitals — another prime target for ransomware — schools cannot afford to be offline for long. This means that the educational sector is more likely to pay out than other industries. In a survey of IT decision makers at nearly 500 schools around the world, conducted by the British security software company Sophos, 35% of those targeted by ransomware paid off the hackers.
But, for cybercriminals, ransoms are not the only potential source of revenue. In addition to demanding fees to decrypt data, they are stealing information and threatening to leak it online if they are not paid.
“On the dark web, identity information for minors and young children is actually more valuable,” explained Levin. “That is because they have a fresh credit record that they can start to abuse and that no one is monitoring.”
So far, Parr-Burman doesn’t believe that any student or staff data was stolen from the Isle of Wight Education Federation, but it has happened to other schools. When Toledo Public Schools in Ohio was targeted by hackers in September 2020, the district refused to pay. Data was dumped on the dark web, including the addresses and social security numbers of current and former students. Months later, one parent was notified that someone had tried to open a credit card in the name of his elementary-school-aged son.

Wide-ranging disruption
As soon as Caroline Sice got the call informing her about the ransomware attack on Lanesend Primary, she snapped into problem-solving mode. She telephoned the school’s chair of trustees, business manager and leadership team to set up a meeting. She then sent an email to teachers, letting them know that she was on the case.
For a moment, it felt like the matter was under control. But, as the scale of the problem became clearer, she started to lose hope.
“Over the weekend, it got heavier and heavier and heavier,” she said. “Suddenly, it begins to dawn on you that you’ve got nothing. Nothing. All the lesson plans. Oh my goodness, how are the teachers going to respond? This is years and years of their work, years of learning. The more you thought of it, the bigger and bigger it grew.”
The hackers also encrypted the backups of all of the data for Lanesend Primary and the five other schools, which meant the easiest way to resolve the problem was off the table. Staff would have to recreate all of the schools’ records from scratch. Then the Isle of Wight Education Federation informed Sice that it would no longer provide data storage or technical support to the primary schools including Lanesend after October 31. On top of recovering from the ransomware attack, Sice now has to find a new place to host all of her school’s information.
Ultimately, Parr-Burman, Sice and the headteachers of the other affected schools made the decision to delay the start of classes by three days, to allow staff time to regroup and bring students back safely amid the pandemic. For the first six weeks of school, everything was done on paper.
Kids are now back at their desks, but the upheaval caused by the attack is far from over. Some of the problems have been minor, like supplies not being delivered because schools could not pay bills after losing all of their financial information. Other things were unexpected. Hackers encrypted access to the digitized bells in one of the secondary school’s buildings, so for the first three weeks of classes, they rang at random intervals. Because the schools lost all their contact lists and access to email, the IWEF couldn’t inform parents or staff that the systems were down and the start of term would be delayed, so Parr-Burman put out a notice in the local paper.
Some of the lost data was more important and more laborious to reassemble. The medical information of staff and students, financial records, payroll details, staff background checks — all of it was gone and none of it has been decrypted.
On top of all the administrative challenges created by the ransomware attack, Caroline Sice is concerned teachers who lost lesson plans that they had devised will be forced to turn to a more rote curriculum.
“We’re a very creative school,” she said. “We learn from what interests the children. So every year is different. I’m worried that actually what they’ll now pull on is just whatever they can get rather than it being what was really made for the children.”
Lanesend has about a dozen students with special needs, who have individual education, health and care plans, a government program to identify a child’s needs and ensure that they are met. It took three weeks, even with two people working on it, to recreate the learning plans for each of those students.
IWEF is facing high costs, as well. To prevent a future attack, the federation will now back up the secondary schools’ data, apart from the three primary schools, on a daily basis and store it separately so it can’t be encrypted during another attack. This will likely cost tens of thousands of dollars a year.
Overall, Parr-Burman estimates the ransomware attack will cost IWEF up to $160,000, plus an additional $53,000 each year for increased security.
Rebuilding databases, lesson plans and records will take hundreds of hours, on top of staff’s other responsibilities. The emotional toll is weighing on Sice and the team at Lanesend Primary. The school’s head of finance resigned recently, owing to stress. Sice says that she is trying to maintain a brave face for the children, but that she has trouble sleeping at night.
“As head teacher, I’ve done some pretty tough things. This is the toughest. And it’s come on the back of Covid,” she said. “It’s challenging because it’s out of my control. It’s out of my expertise. And I’m relying on other people to try and get it back together. I would say it’s bent me towards breaking.”
The story you just read is a small piece of a complex and an ever-changing storyline that Coda covers relentlessly and with singular focus. But we can’t do it without your help. Show your support for journalism that stays on the story by becoming a member today. Coda Story is a 501(c)3 U.S. non-profit. Your contribution to Coda Story is tax deductible.














